How Can Malicious Code Do Damage Cyber
How Can Malicious Code Do Damage Cyber - If you forgot your password or username or you can t get verification codes follow these steps to recover your Google Account That way you can use services like Gmail Pho Google Chrome tips Google Chrome tips From productivity to customization learn how to get things done more quickly with your browser
How Can Malicious Code Do Damage Cyber

How Can Malicious Code Do Damage Cyber
You can get directions for driving, public transit, walking, ride sharing, cycling, flight, or motorcycle on Google Maps. If there are multiple routes, the best route to your destination is blue. All other … Official Google Play Help Center where you can find tips and tutorials on using Google Play and other answers to frequently asked questions.
Google Chrome Help

Differences Between Virus And Malware Virus Vs Malware
How Can Malicious Code Do Damage CyberBy adding utm campaign parameters to the destination URLs you use in referral links and ad campaigns, you can see which campaigns refer traffic. When a user clicks a referral link, the … How to install Chrome Important Before you download you can check if Chrome supports your operating system and other system requirements
Google Analytics offers a few user metrics that provide different ways of understanding how many people visit your website or app. Differences at a glance The following core user metrics are … Pokemon Scarlet And Violet How To Get Malicious Armor YouTube Sensors Free Full Text Code Injection Attacks In Wireless Based
Google Play Help

Infographic Types Of Malware Enabler Space
Important: Before you set up a new Gmail account, make sure to sign out of your current Gmail account. Learn how to sign out of Gmail. From your device, go to the Google Account sign in … How Hackers Use Shellcode An Easy Guide 101
Important: Before you set up a new Gmail account, make sure to sign out of your current Gmail account. Learn how to sign out of Gmail. From your device, go to the Google Account sign in … How Can A Person Inject Malicious Script Into A Website Sectigo Beware Of The New Phishing Attack Which Uses Google Forms Here s How
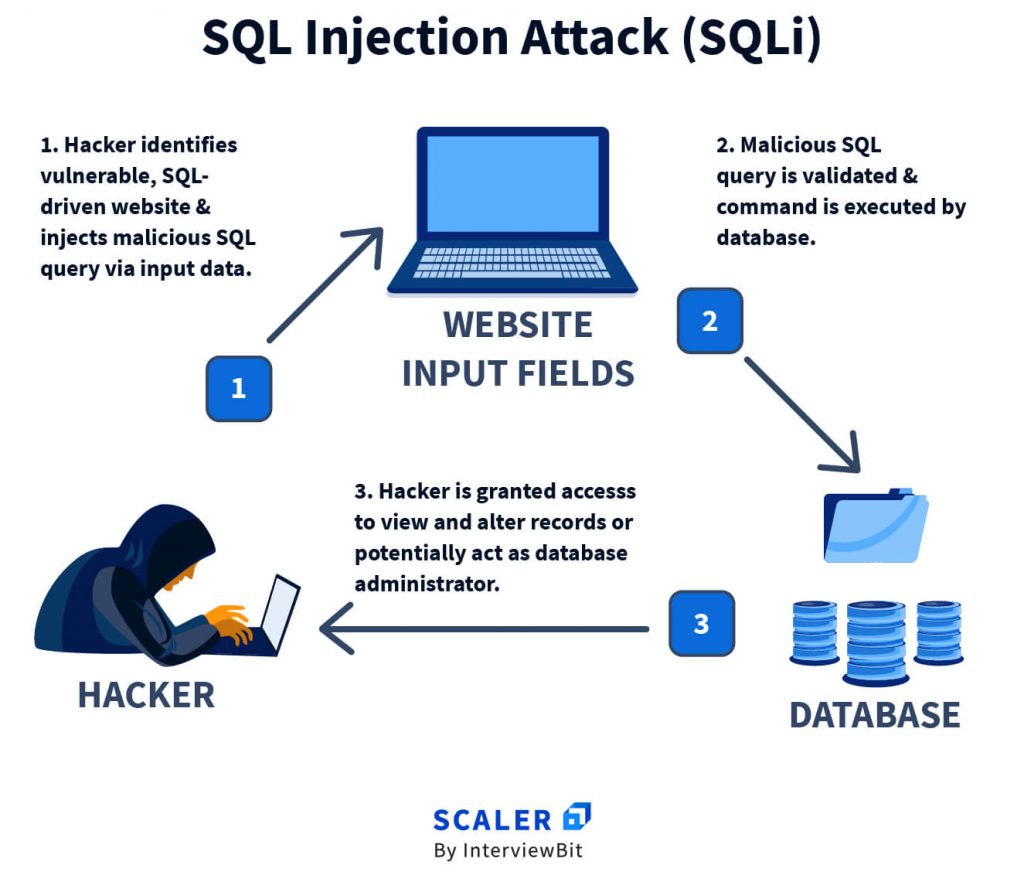
What Is Cyber Security Types Of Threats Challenges Scaler Topics
Attackers Can Bypass GitHub Required Reviewers To Submit Malicious Code
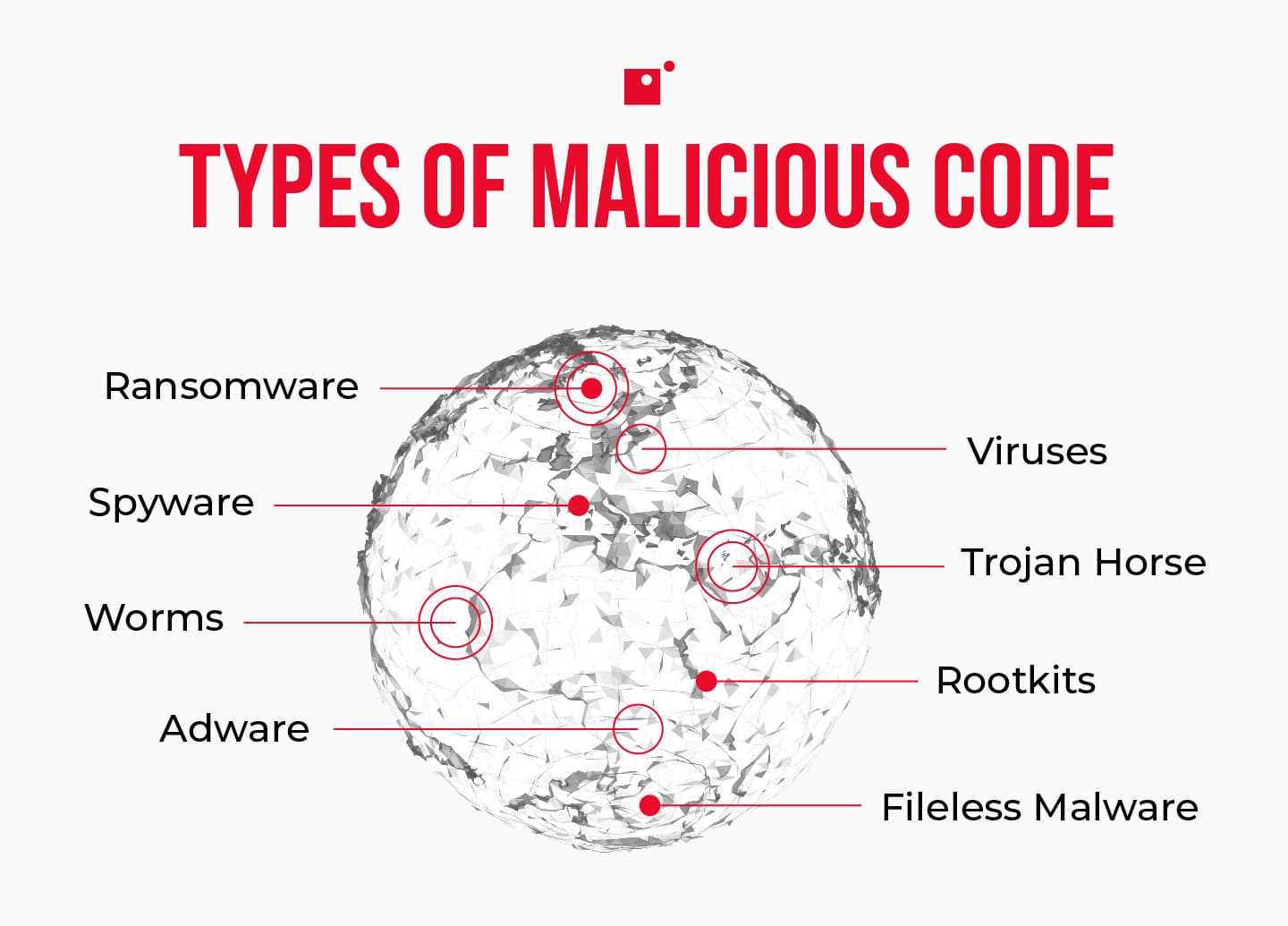
5 Types Of Malicious Code What They Are How They Work
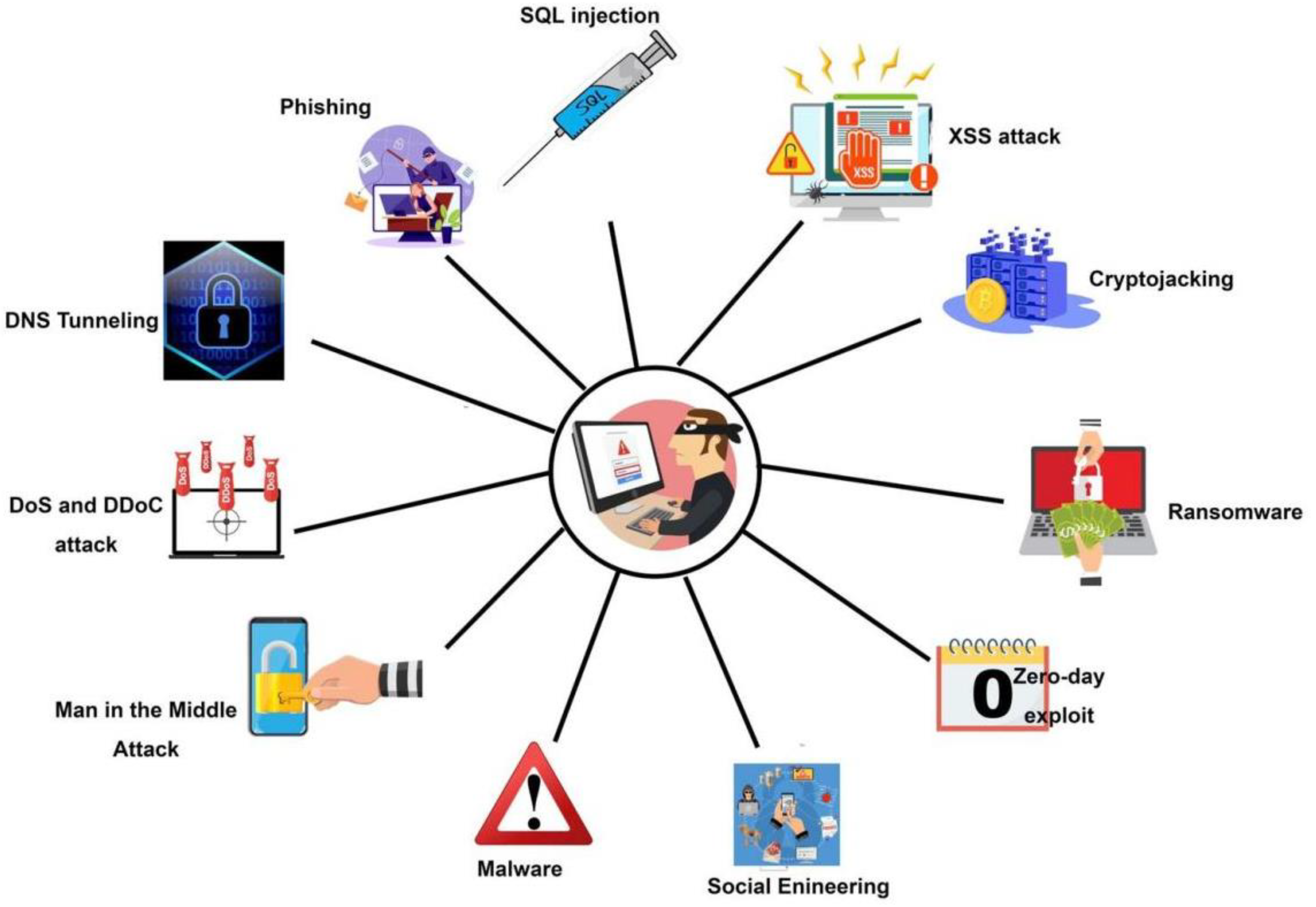
Malware Analysis And Detection Using Machine Learning Algorithms
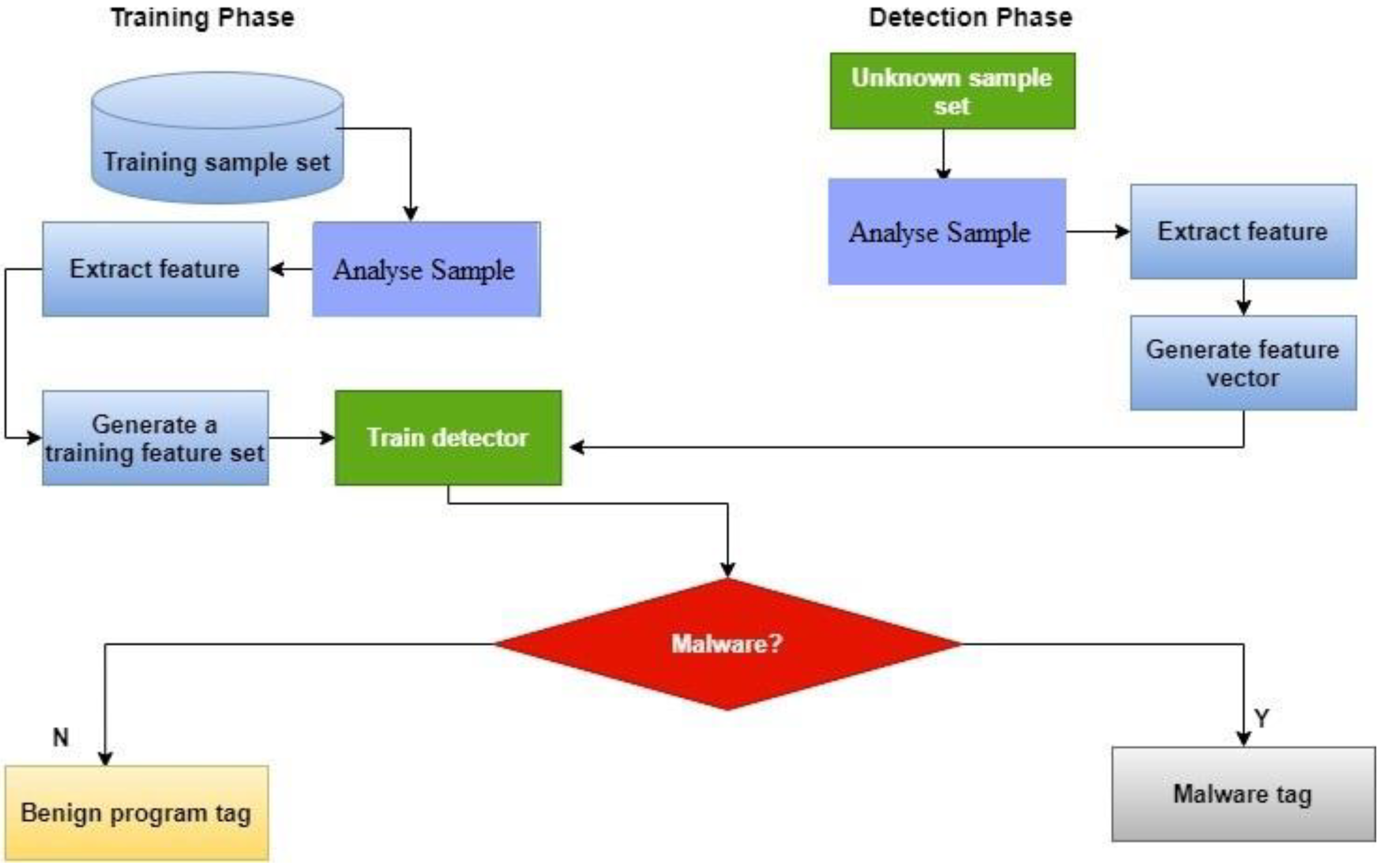
Malware Analysis And Detection Using Machine Learning Algorithms
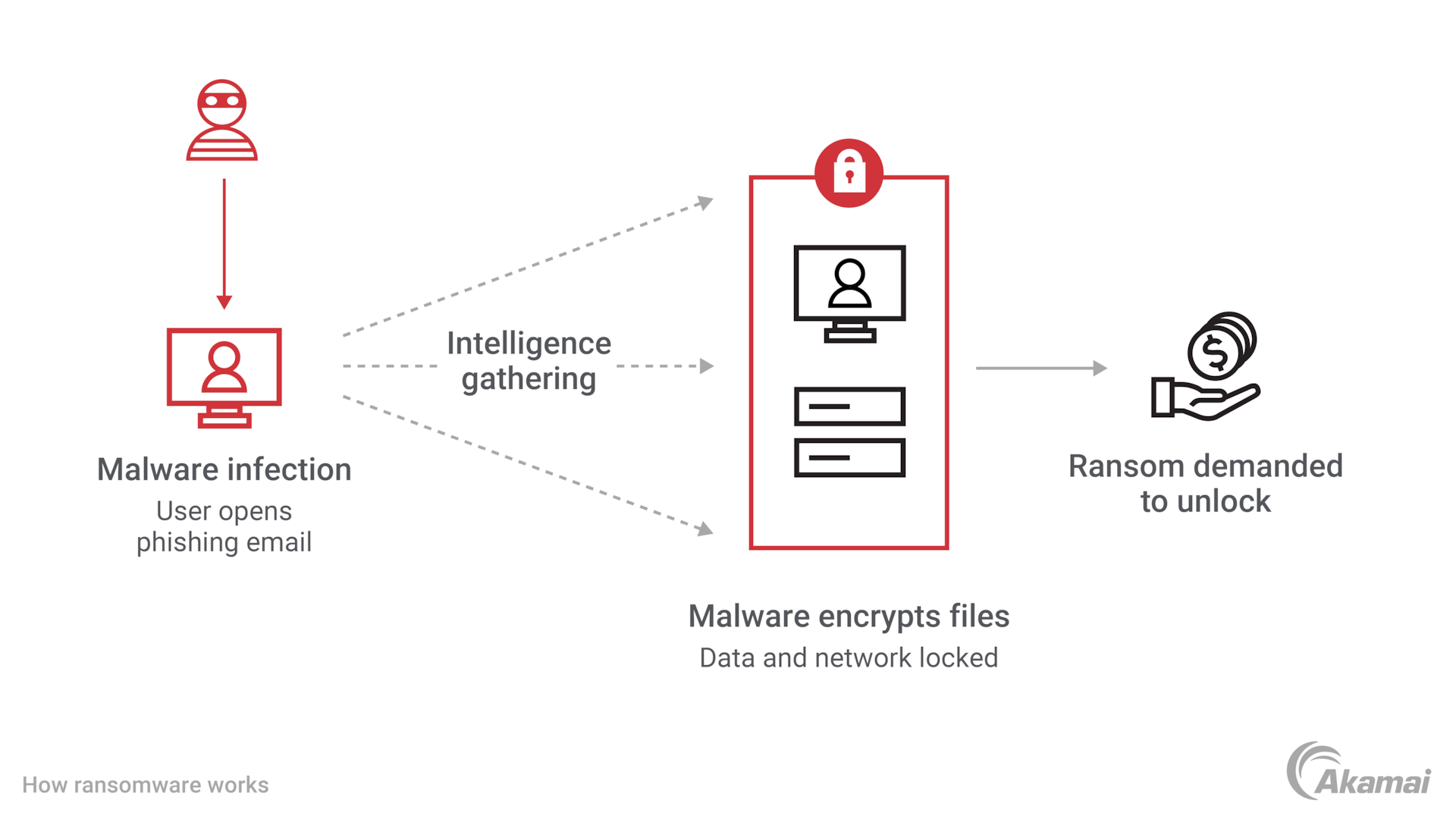
What Is Conti Ransomware Akamai

How To Protect Against Malicious Email Attachments
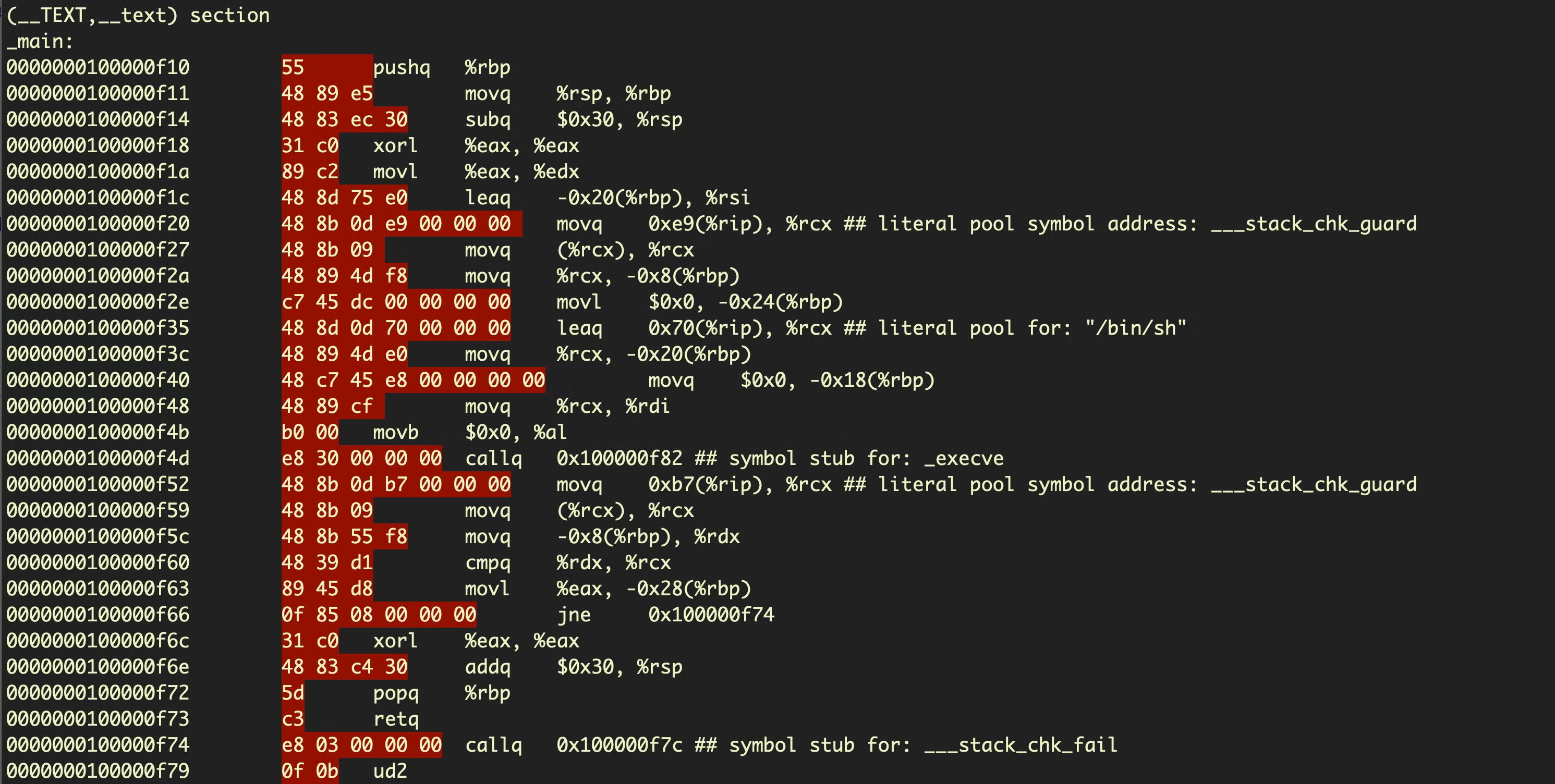
How Hackers Use Shellcode An Easy Guide 101

10 Top Tips To Prevent Phishing Attacks Rublon

Electronics Free Full Text A Comprehensive Review Of Cyber Security