What Is Spoofing In Cyber Security
What Is Spoofing In Cyber Security - What is Spoofing in Cyber Security An attack that appears like a legitimate one that traps people to fall into their hands and gives way to steal confidential information or data is called Spoofing In simple words Spoofing is not but a method to gain important or sensitive information from people behaving like genuine people or In email spoofing a cyber criminal uses a fake email address to commit a malicious act Depending on the email spoofing tactic they may spoof the email address email sender s name or both Additionally the cyber criminal can assume multiple identities the sender the company or both
What Is Spoofing In Cyber Security
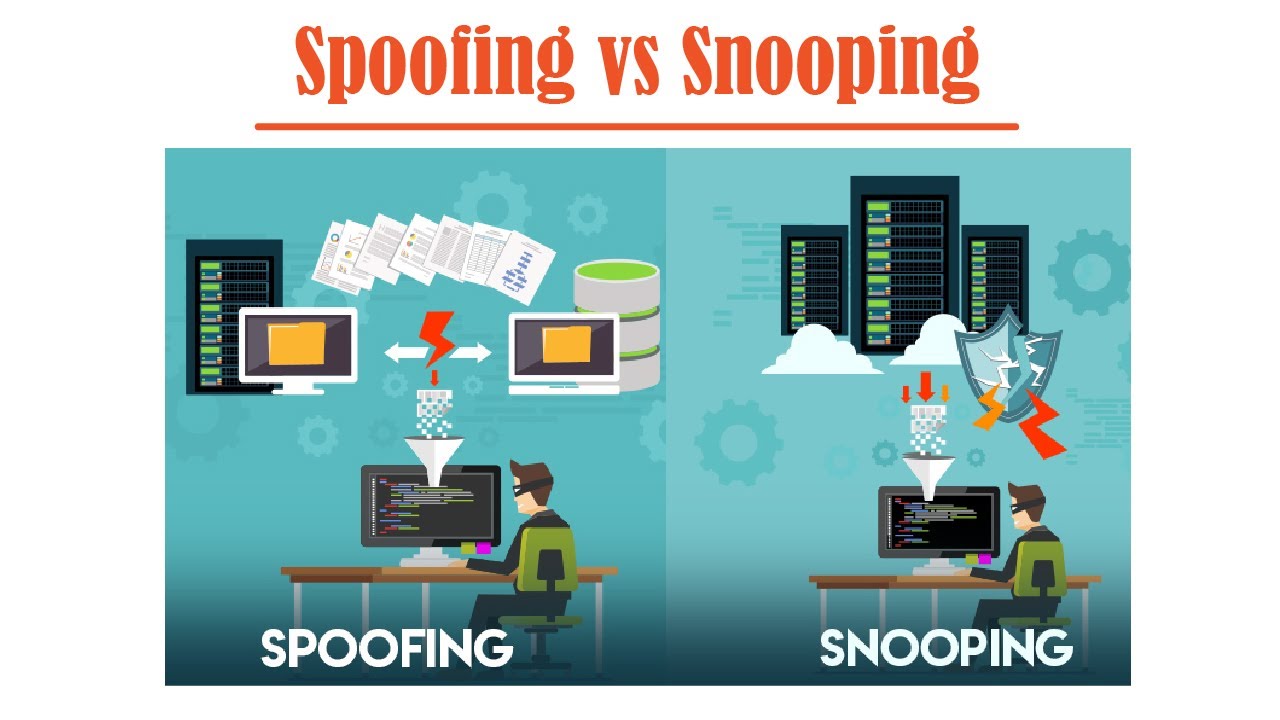
What Is Spoofing In Cyber Security
Spoofing is a broad term for the type of behavior that involves a cybercriminal masquerading as a trusted entity or device to get you to do something beneficial to the hacker — and detrimental to you. Any time an online scammer disguises their identity as something else, it’s spoofing. Spoofing is a technique through which a cybercriminal disguises themselves as a known or trusted source. Spoofing can take many forms, such as spoofed emails, IP spoofing, DNS Spoofing, GPS spoofing, website spoofing, and spoofed calls.
What Is Spoofing Examples amp Prevention Terranova Security

Buddy Mears
What Is Spoofing In Cyber SecuritySpoofing is a type of cybercriminal activity where someone or something forges the sender's information and pretends to be a legitimate source, business, colleague, or other trusted contact for the purpose of gaining access to personal information, acquiring money, spreading malware, or stealing data. Spoof protection (2:18) Cisco Secure Email Oftentimes spoofing is used during a cyberattack to disguise the source of attack traffic How Spoofing Works Spoofing happens when cybercriminals use deception to appear as another person or source of information That person can manipulate today s technology such as email services and messages or the underlying protocols that run the
To effectively protect against spoofing attacks, organizations and individuals should implement proper security measures, such as email authentication protocols (SPF, DKIM, DMARC), network monitoring, encryption, and security awareness training. Spoofing is a cyber-attack on the rise, so it’s critical to be vigilant and verify the . What Is Spoofing Definition Examples Prevention Tips Email Spoofing Attack
What Is Spoofing Spoofing Attacks Defined CrowdStrike

What Is Spoofing How It Works Cyber Security News
Active Shooter Safety Resources Spoofing and Phishing Spoofing Spoofing is when someone disguises an email address, sender name, phone number, or website URL—often just by changing one. What Is Spoofing How Does It Work Security Tips
Active Shooter Safety Resources Spoofing and Phishing Spoofing Spoofing is when someone disguises an email address, sender name, phone number, or website URL—often just by changing one. Email Spoofing Attack Email Spoofing Attack

Definition Oof Spoofing Store Emergencydentistry
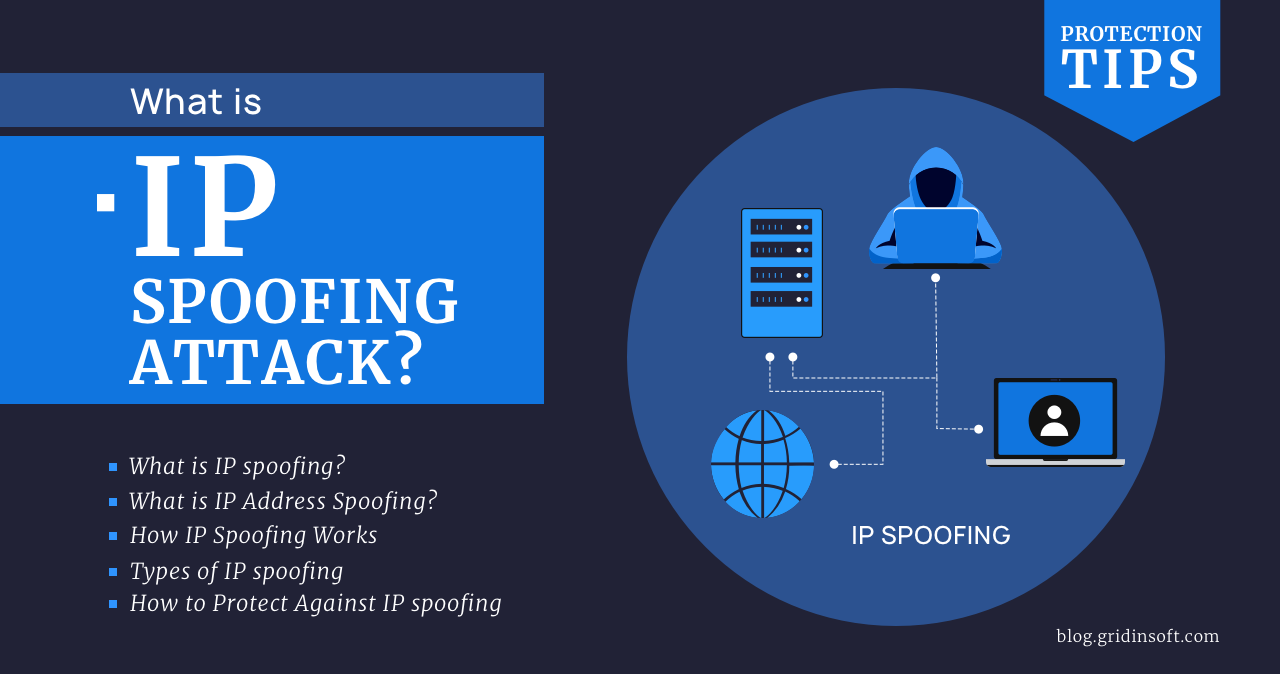
Definition Oof Spoofing Store Emergencydentistry

Spoofing Meaning Examples Types Prevention Vs Phishing
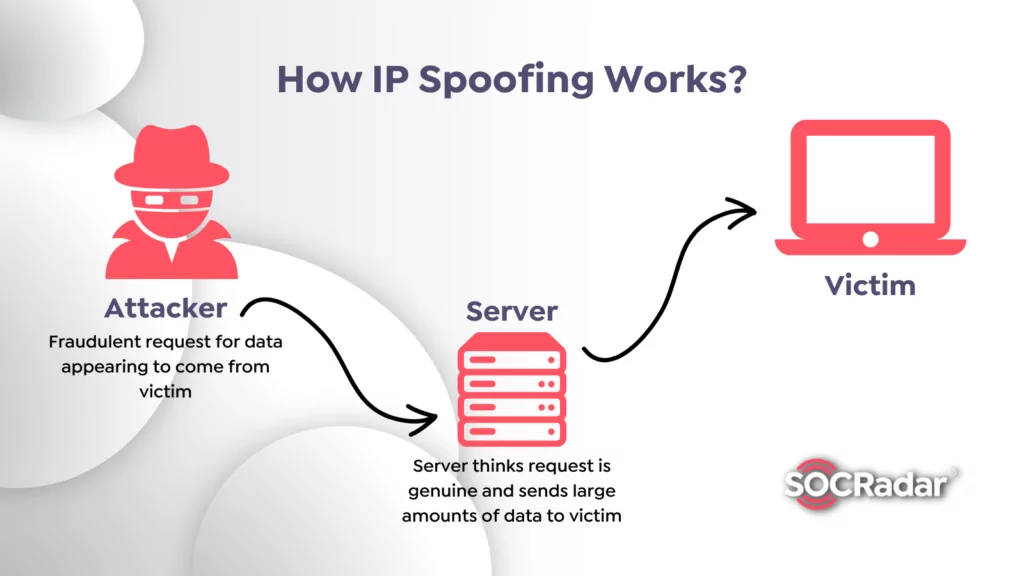
Ip Spoofing

Web Spoofing

Web Spoofing
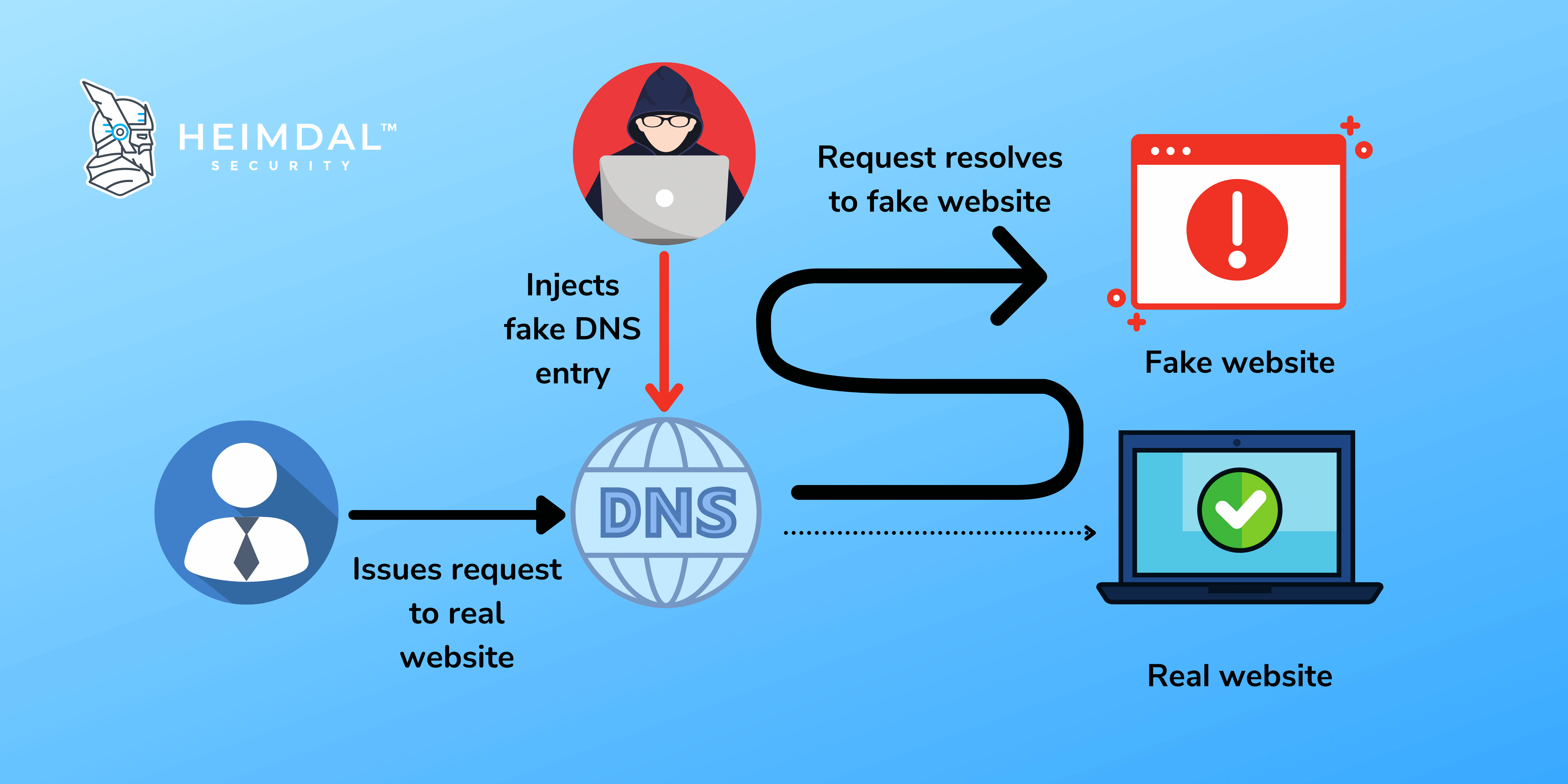
Web Spoofing
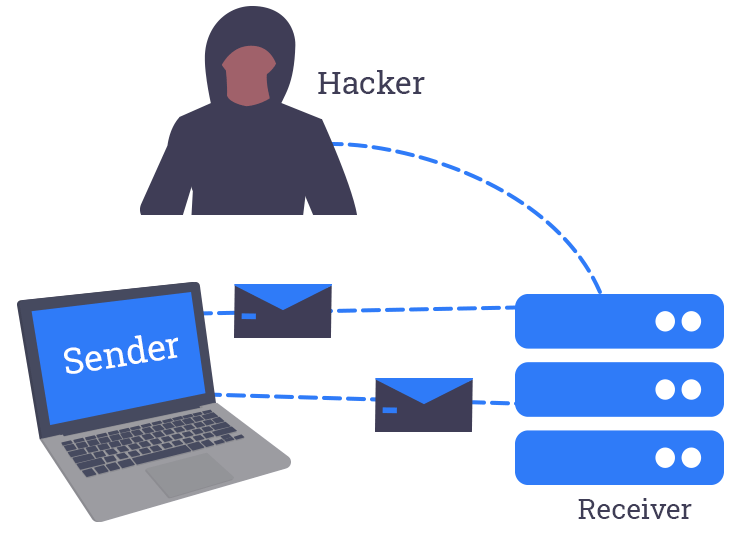
What Is Spoofing How Does It Work Security Tips

Email Spoofing Attack
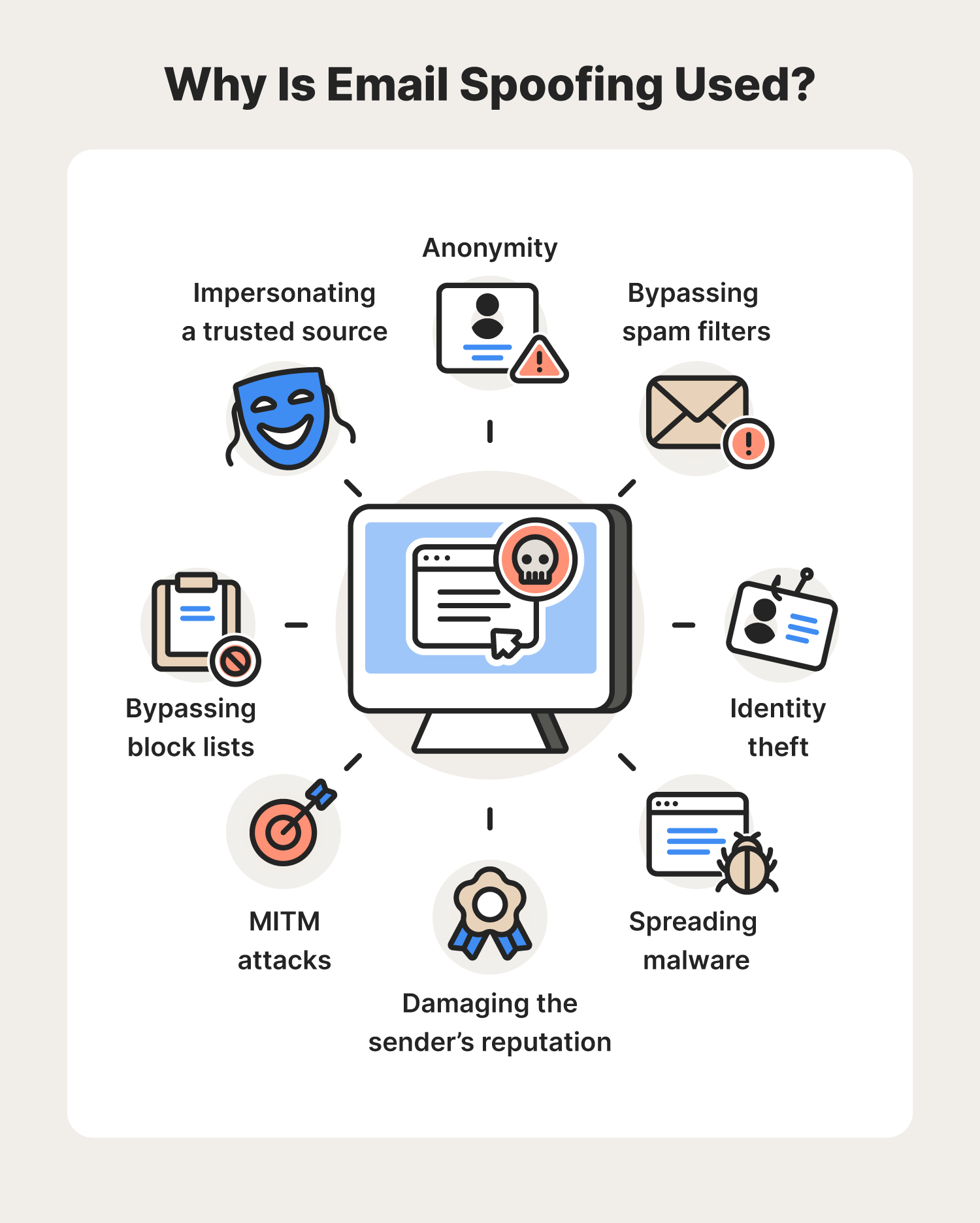
Email Spoofing Attack